What is a phishing scam?
A phishing scam is any attempt to fraudulently obtain personal information or bank details, and involves a cyber criminal posing as a trustworthy entity or company. These online scams are often carried out over email, and nearly always have malicious intent behind them.
Cyber criminals deceive the email receiver with empty threats, harmful links, and often act as well-known companies. They can then steal your business’ sensitive information, or make unauthorised payments with your details - leaving your business in an undesirable situation.
A phishing scam email will look something like this:

Netflix phishing scam
Late 2017, Netflix subscribers were
targeted by a phishing scam. Users were hit with an email trying to trick them into thinking that their accounts were going to be suspended.
The targeted and personalised emails told users that they’d need to update their billing information, and must ‘restart their membership’, if they wanted their subscription to continue. The deceptive email also had a link to a fake Netflix site, which it urged users to click on.
Netflix has over
109 million worldwide subscribers, all of which were in danger of having their credit card details stolen.
Qatar Airways phishing scam
In the first quarter of 2017, businesses in Qatar were targeted with
93, 570 phishing attacks in just a three-month period. Qatar’s phishing attacks involved the hackers sending out malicious emails and SMS texts to businesses, designed to compromise valuable information and data.
The big question, how many of them were wise to phishing scam emails?
What are spear phishing threats?
These are more successful than random phishing threats. The victim is specifically targeted by the cybercriminal with specific and personal information. This may be obtained from social media, and is often so personal that it often convinces the receiver that the email must be legitimate.
For example, RSA was attacked using a Flash object embedded in an Excel file that was attached to an e-mail with the subject line
“2011 Recruitment Plan”. Small groups of employees were targeted, and the e-mail was filtered and landed in the users’ junk mail folder. It only took one employee to fall for the targeted scam.
The
Symantec Report suggests that 55% of spear fishing attacks were executed successfully last year.
How do phishing scams work?
Phishing scams exploit human weakness rather than technology. This is much easier as people are more likely to be successfully manipulated.
In general, the scams can work as they can target a high number of people. In 2016, it was the most common type of attack, which affected
1,299,178 businesses.
If you are aware of these risks to your business, then you are likely to avoid any disaster.
How to recognise phishing scam emails
The number one rule is to always take the precautions before clicking on a link which has been plugged into an email.
If you’re suspicious about the email, simply hover the mouse of the link (don’t click), and see if the address matches the one in the email. If not, then it’s likely to be a scam.
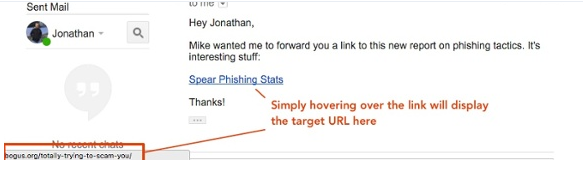
(Image from Barkly)
- Spoofs of well-known websites and companies
The email will often include a web address which resembles a well-known one, but include a slight alteration. The graphics, design, and logo may appear the same at a quick glance.
So, if the email is asking you to take actions which are out of the ordinary, look out for differences compared to the real brand. You may have a legitimate email from the company, person, or site before, so could compare the two.
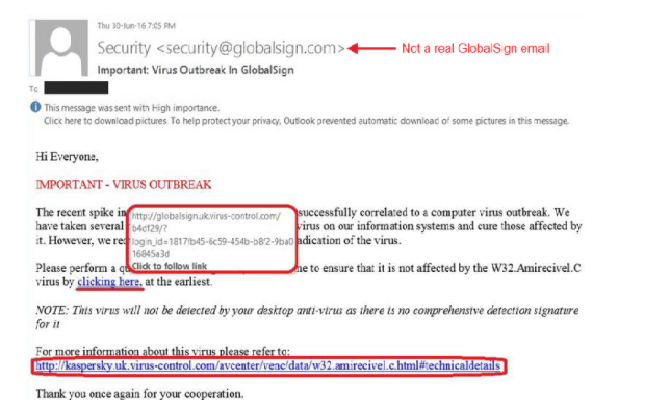
(Image from GlobalSign)
- Grammatical errors and spelling mistakes
A legitimate company will usually have experienced copywriters sending out their emails, which will have been carefully proofread by an expert. Cybercriminals may be able to orchestrate a huge scam, but their spelling and grammar often gives them away.
Spotting these mistakes can be one of the simplest ways to detect a scam email.
In the following example, there is a comma in the wrong place in the greeting, and the sentence structure is awkward.
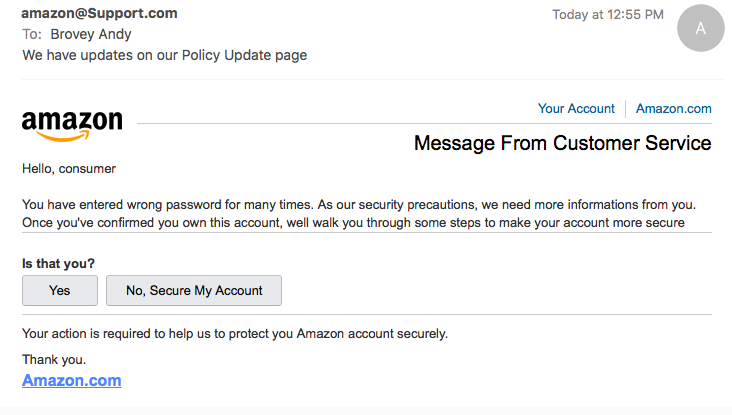
(Image from The Stratford Board of Education)
Threats can make people react quickly. Consider whether the threat has any truth or reality to it. Ironically, fraudsters will often use threats that your security has been compromised.
An example of one of the most common threats is ‘’Verify your account or we’ll close it!’’.
If the email contains one or more of these features, then you need to question whether it’s from a reputable source.
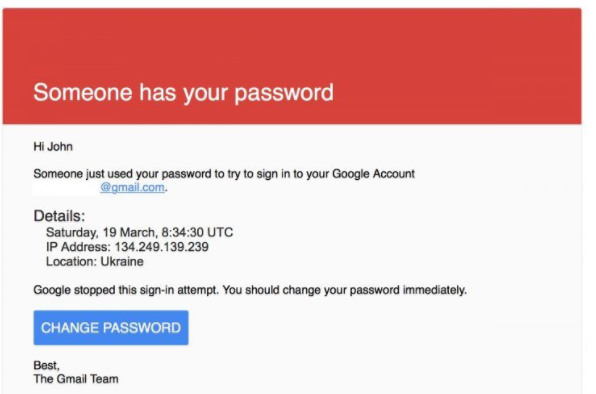
(Image from Yahoo Finance)
How to protect yourself from phishing scam emails
Prevention is the best solution. Educate your employees on how to identify a phishing scam email (see above).
The effects of a successful scam on your business could be disastrous. The damage of a breach could leave your business seriously out of pocket. If you educate all employees on scam emails, and what to look out for, then the likelihood of someone opening a dodgy link or entering sensitive data will be decreased.
You should also have an effective
IT security policy in place.
There is anti-virus and firewall software available which will detect, filter out, and protect you against some of these threats.
However, it’s important to remember that these are not 100% effective, and extra precaution will also have to be taken. Spear fishing emails are particularly good at finding their way through this software. Once the email is received in your employee’s inboxes, then your company’s security is in their hands.
So, you must take the time to educate them on the best practices to prevent security disasters.
If you want to learn more about cyber security and how to protect your business, then
contact our friendly team today for a chat today.

 (Image from Barkly)
(Image from Barkly)
 (Image from GlobalSign)
(Image from GlobalSign)
 (Image from The Stratford Board of Education)
(Image from The Stratford Board of Education)
 (Image from Yahoo Finance)
(Image from Yahoo Finance)